Perfect How To Make Vulnerability Assessment Report

Vulnerability Assessment Report.
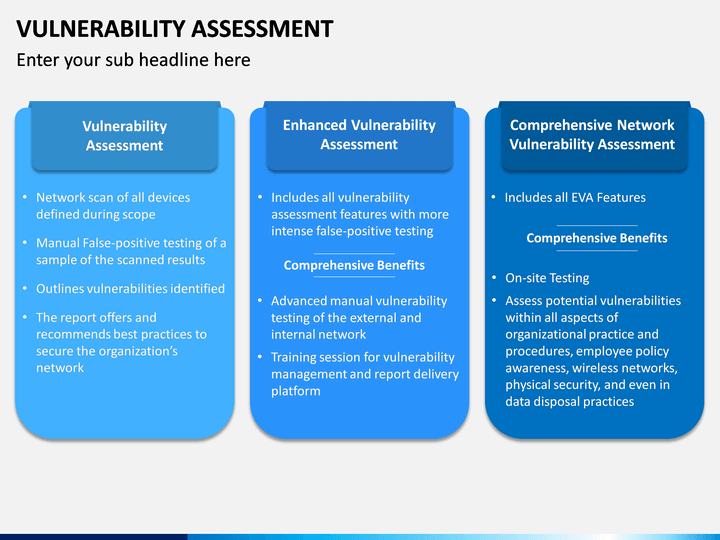
How to make vulnerability assessment report. Is vulnerable to more than one threat or. Finally a report will need to be created at the end of the scan. Prioritize and remediate imminent and impactful risks with Vulnerability Manager Plus.
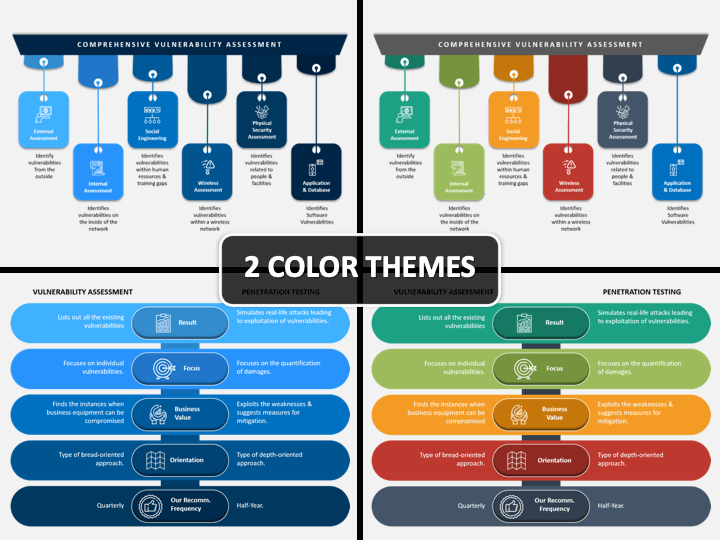
Understand that an identified vulnerability may indicate that an asset. AIndex Content of Vulnerability Scan B. Ad Discover the Key Features of IBM Guardium Vulnerability Assessment.
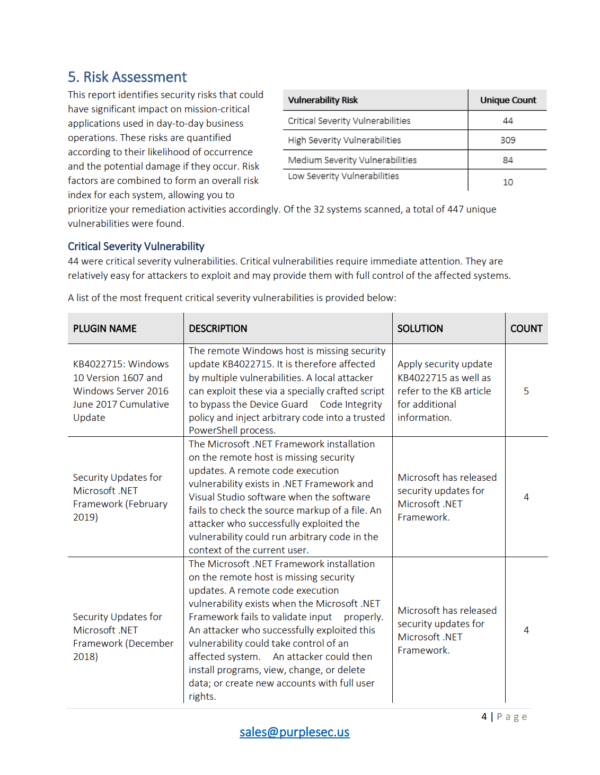
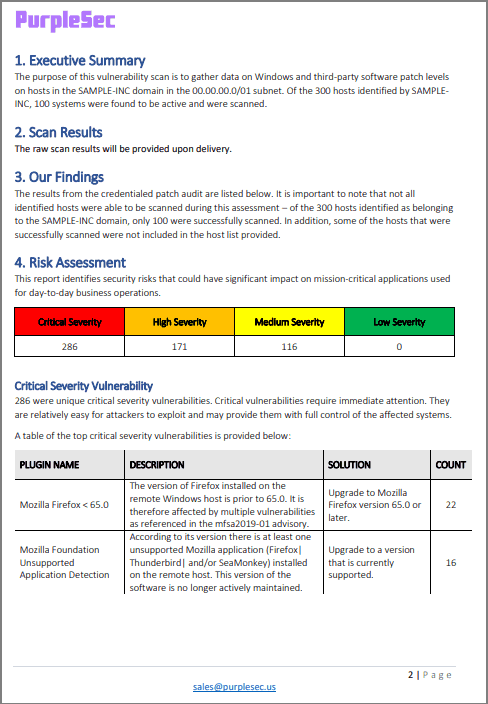
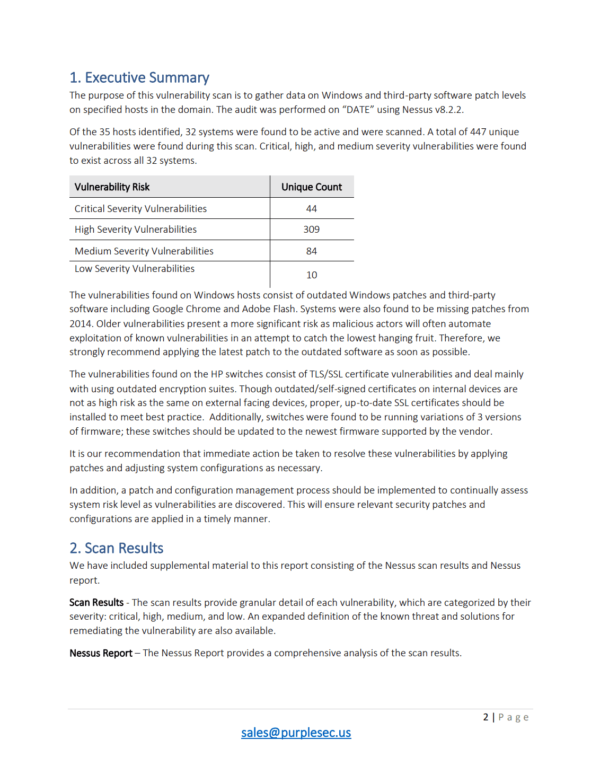
Risk Assessment This report identifies security risks that could have significant impact on mission-critical applications used for day-to-day business operations. Totally free Templates For You. In the Azure portal open the specific resource in Azure SQL.
November 15 2020 by lesboucans. Prioritize and remediate imminent and impactful risks with Vulnerability Manager Plus. The Web has hundreds associated with.
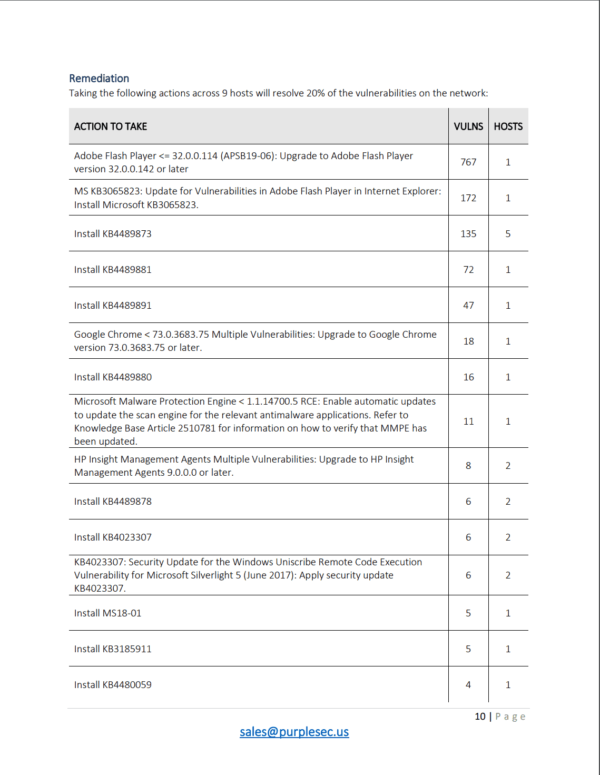
A vulnerability assessment report details issues around threats and risk however it is critical to identify threats before a comprehensive vulnerability analysis can be justified. Ad Proof Of Exploit Technology Eliminates The Need For Manual False Positive Verification. Tips for a Stronger Vulnerability Assessment Report 1.
No Matter Your Mission Get The Right Defect Tracking Tools To Accomplish It. Guardium Vulnerability Assessment Identifies Threats Security Gaps in Databases. Ad Discover the Key Features of IBM Guardium Vulnerability Assessment.